Endpoint Detection and Response (HX)

Endpoint detection and response (EDR)
Every day brings a new cyberattack, a new vulnerability, or a new ransomware
target. Security teams find it increasingly difficult to keep up with the threats
to their users, company data, and intellectual property and don’t always bring
in extra help. Responders are burdened with too many tools that do not work
together and create more noise than useful signals. Systems in place do not always provide adequate detection and response of these advanced threats.
FireEye Endpoint Security defends against today’s cyberattacks by enhancing the best parts of legacy security products with FireEye technology, expertise
and intelligence. Using a defense-in-depth model, the modular architecture of Endpoint Security unites default engines and downloadable modules to protect, detect and respond, and manage endpoint security.
To prevent common malware, Endpoint Security uses a signature-based
endpoint protection platform (EPP) engine. To find threats for which a signature does not yet exist, Malware Guard uses machine learning seeded with knowledge from the frontlines of cyberattacks. For attacks on exploits in common software and browsers, Exploit Guard uses a behavioral analysis
the engine that determines if an exploit is being used and stops it from executing.
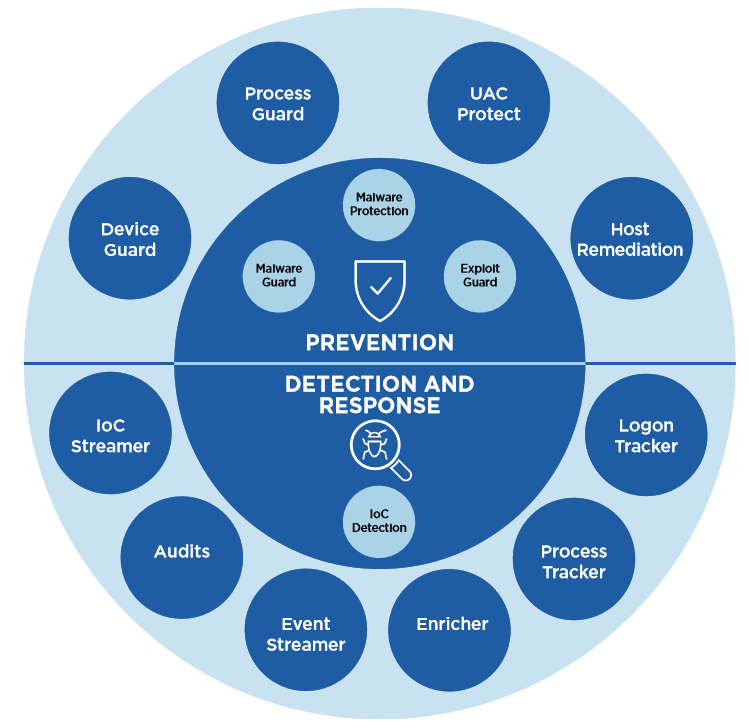
In addition, FireEye continuously creates modules to detect an attack techniques and accelerate responses to emerging threats. For example, Process Guard was developed to stop credential exfiltration.
Endpoint Security includes endpoint detection and response (EDR) capabilities that rely on real-time indicators of compromise (IOCs) developed with help from frontline responders. FireEye tools also:
• Search for and investigate known and unknown threats on tens of thousands of endpoints in minutes.
• Identify and detail the vectors an attack used to infiltrate an endpoint
• Determine whether an attack occurred (and persists) on a specific endpoint and where it spread.
• Establish timeline and duration of endpoint compromises and follow the incident.
